
Today we are releasing some major new features across all our products: Web Application Firewalls (WAF) and Advanced Traffic Management.
WAF is an HTTP-level firewall that protects your application against well-known attacks and exploits. Using WAF, you can block traffic to your applications from certain origins and detect and block specific attacks from reaching your application.
GeoIP WAF
Let's start with blocking traffic by country of origin (GeoIP WAF). Allowing or blocking traffic from certain countries is as simple as selecting them on the Traffic Filters page. GeoIP WAF works by using IP-to-country mapping on your servers, which is fast and doesn't add overhead to the client calls.
OWASP Rules
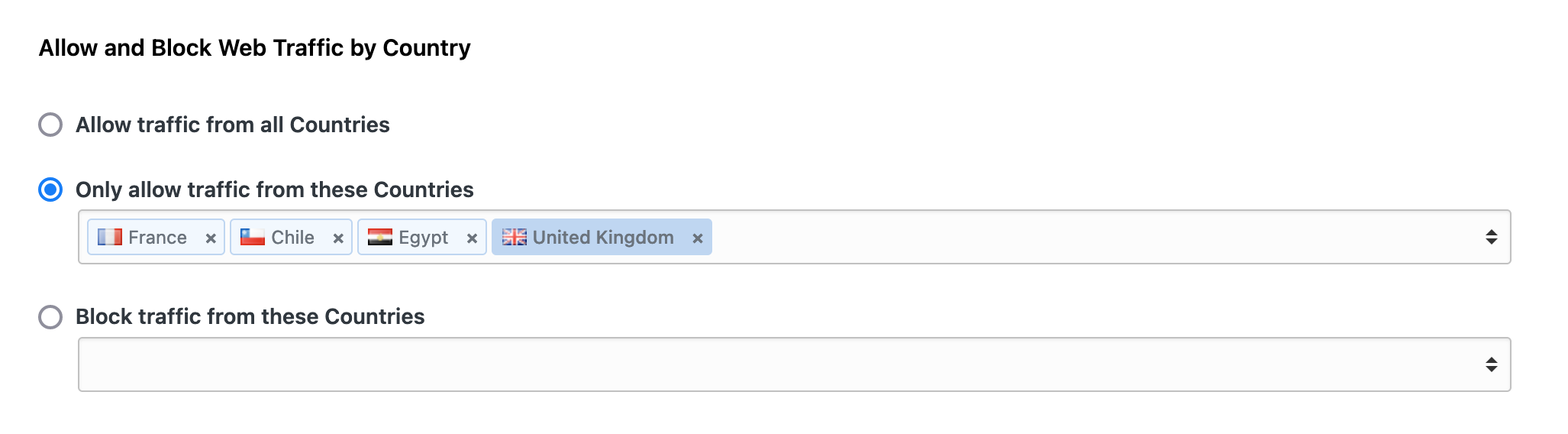
Open Web Application Security Project, or OWASP for short, is a nonprofit foundation that promotes web application security. OWASP has compiled a list of known attacks and web exploitations that are known as OWASP Rules. Blocking traffic that is trying to identify the frameworks running on your servers or trying to inject SQL code are some examples of OWASP rules.
You can now enable any of these rules on your Cloud 66 applications, quickly and easily. Head to OWASP Rules tab under the Traffic page of your application and enable or disable OWASP rules as needed. You can also fine-tune these rules directly in the OWASP configuration file using our (version controlled) CustomConfig system.
Web Traffic Filtering
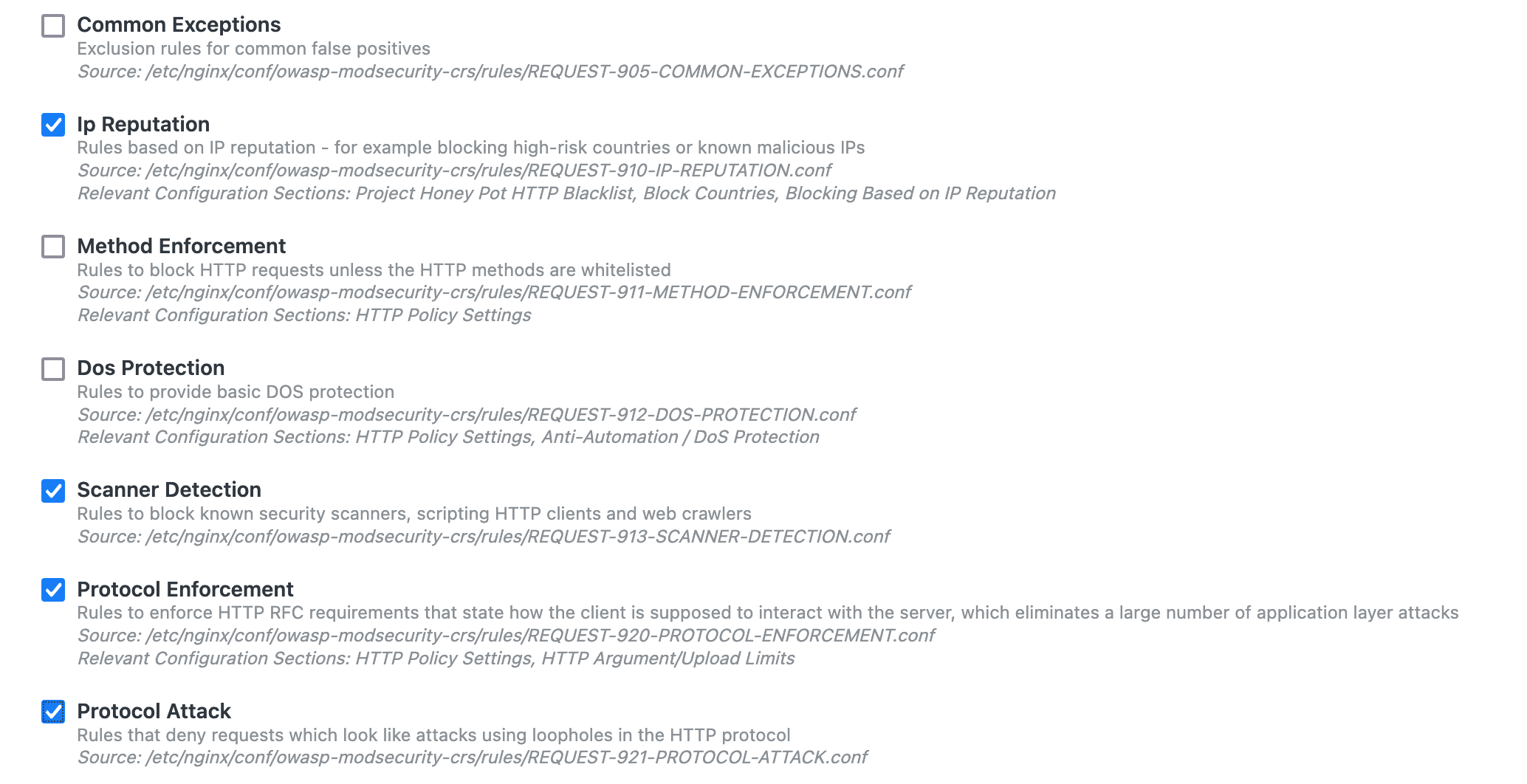
Web Traffic Filtering is another key benefit of WAF. Web traffic can be allowed or blocked from specific source IPs or a list of IPs dynamically fetched from a source. For example, you might want to allow traffic only from a single IP address (like your home router). This is done by adding your home IP address to the Traffic Filters allow list.
Some lists of IPs are dynamic — for example, the list of a CDN's endpoints. Traffic filters can call a URL as a source . Your application will fetch the complete list of IPs from that URL. Paste in the URL in the appropriate field under Traffic Filtering, and you are ready to go.
Surge Protection
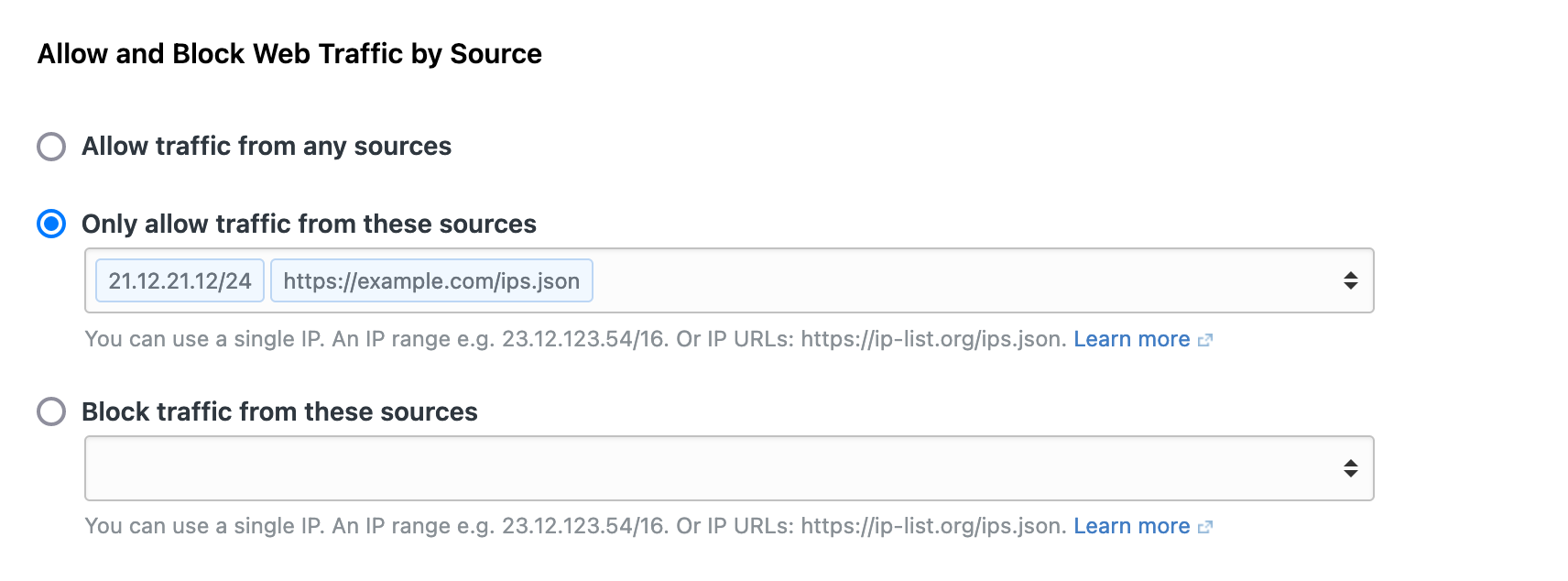
Another aspect of WAF is what we call Surge Protection. By default, repeated attempts to access your application from the same source will be temporarily blocked to protect your application from the extra load and performance degradation. While you can disable this feature, you can also exclude certain IPs or vendors from being blocked by Surge Protection. For example, Surge Protection has native support for Cloudflare and AWS Cloudfront CDN endpoints. Traffic flowing from those networks will not be blocked by Surge Protection.
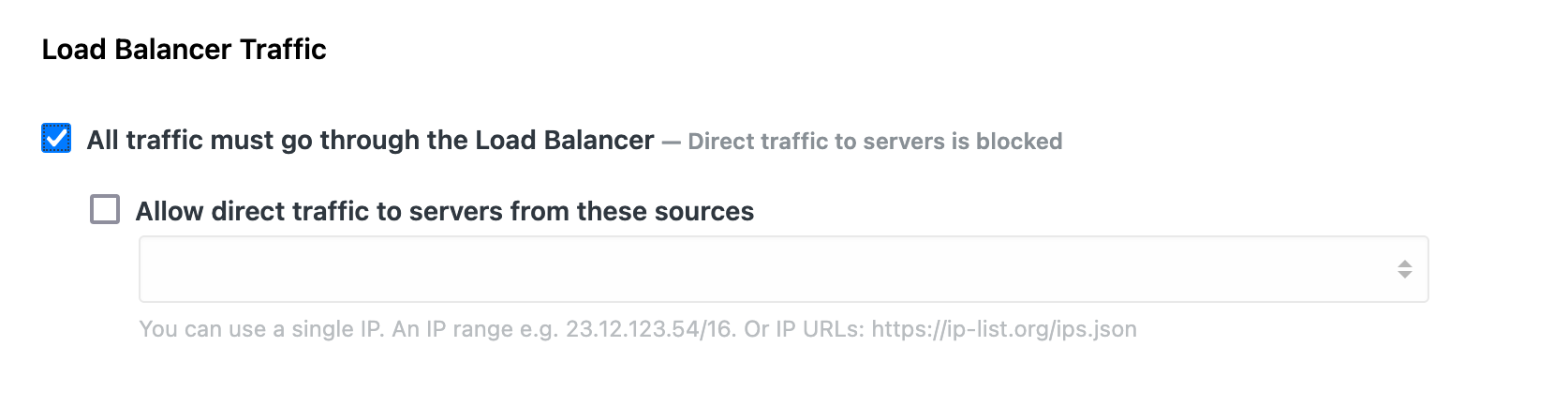
Load Balancer Traffic Enforcement
This is a simple, yet useful feature that blocks direct traffic to your web servers and only allows web traffic to reach your web servers if it comes through one of your load balancers. With native support for cloud load balancers and built-in HAProxy support, enabling this feature is as simple as clicking a checkbox on the Traffic Filters page of your application.
If you need to reach your web servers directly from specific IPs (for example, your development machine or your office network), you can do this by excluding those from Load Balancer Traffic Enforcement.
Summary
Web Application Firewalls, GeoIP traffic restriction, Web Traffic filtering, and Load Balancer Traffic Enforcement are part of the second phase of our new network layer feature (we rolled out Application Private Networks as the first phase last month). We think the added security and improved high availability that these features bring your applications are a great addition to our already rich feature-set, and we are not done yet! So stay tuned for even more useful and exciting features for your applications and your teams.
