We're excited to announce support for inter-stack firewall rules. This has been in development for some time, but was held up by other feature dependencies (which have since been implemented). The feature is now available on all stacks!
What are inter-stack firewall rules?
A fairly common pattern some users follow is where they run a master stack which has some resource that's shared with other stacks. Take for example a stack with a PostgreSQL database, that's then used as the data source for another stack for reporting purposes. Up until now, the only way to handle this inter-stack communication would be to manually open the PG port on the master stack's PostgreSQL server, to allow the IP address of the reporting stack to access it.
This works in theory, but it has three major problems:
- It's a manual and error prone operation (it's easy to use the wrong IP address and hard to know you've made an error)
- If the server IP address changes (physical server instance changed on the cloud; or static IP applied for example), then the rule needs to be updated manually.
- If you scale up/down other servers to the web cluster, then you need to remember to manually amend the firewall rules on your master stack.
The good news is that the above problems are all solved by the new inter-stack firewalls feature.
How do I use them?
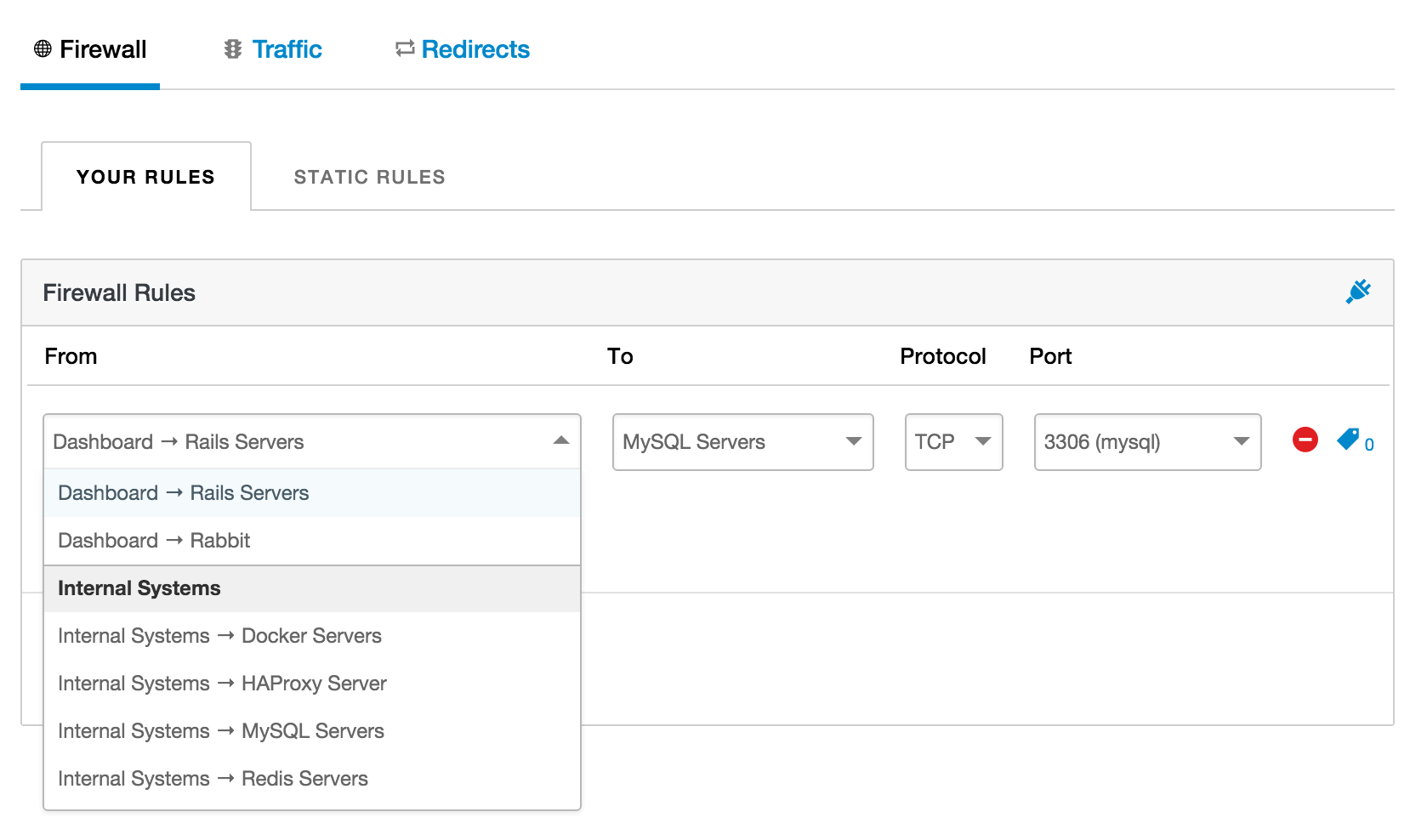
The new features are available to all existing customers, and can be accessed through the Firewall Dashboard via the Network Settings stack menu item.
If you have any other stacks available on your account, when you now select a source for your rules, you'll be able to select a different stack's server groups or servers. This means we'll automatically keep the firewall open to the resources of the other stack, handling all the change events gracefully.
If your other stack exists within the same cloud provider and region, then we'll open the master stack firewall to the internal IP addresses and external IP addresses of your other stack's resource. If they're in different regions or cloud providers, then we'll only allow-in the external IP addresses of your other stack.
It's worth noting that you can type freely to filter the dropdown to particular stacks, or resources. You can of course still enter manual IP addresses should you wish.
Here at Cloud 66 we're constantly looking for ways to improve our service and make the day-to-day of our users easier! Let us know what your think of the new feature :)
If you have any feedback or suggestions, please get in touch and let us know your thoughts.
