
Security! Every company says it's their highest priority, until you realize what they mean by that: stupid password policies.
At Cloud 66 we think security is more than a mix of uppercase and lowercase characters in a password. Here is a quick run down of Cloud 66 security features:
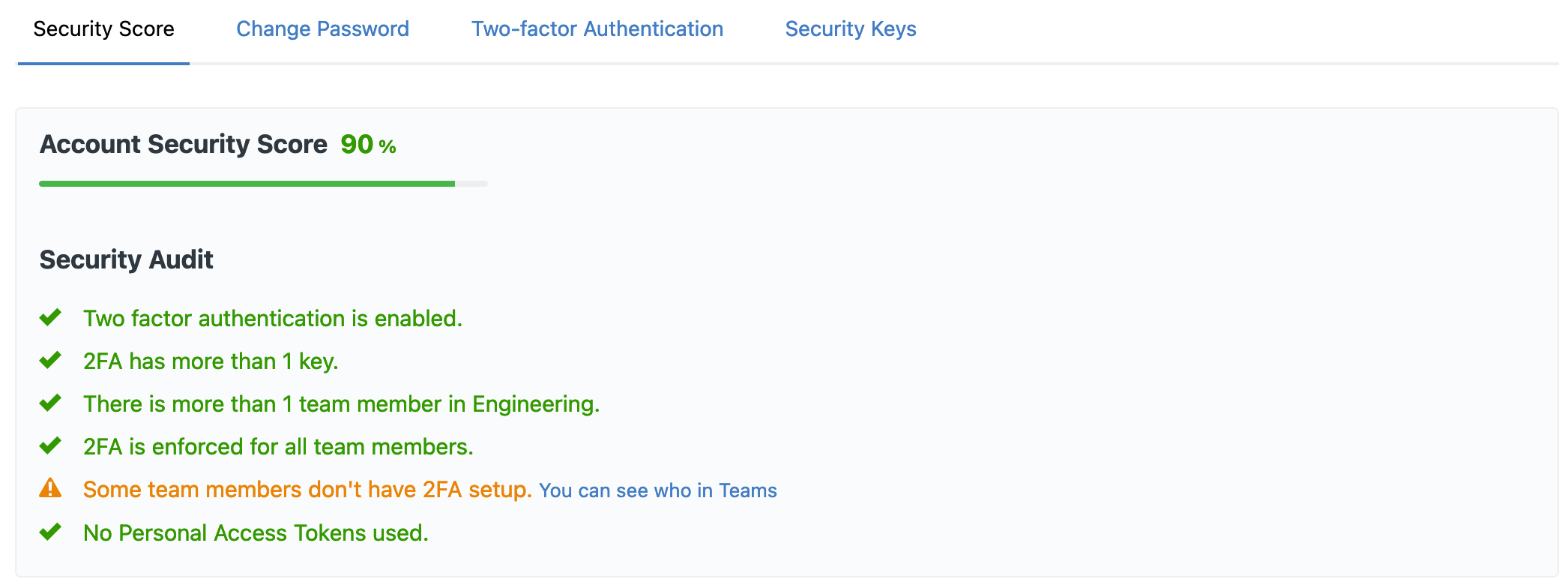
Two Factor Authentication
Cloud 66 supports two factor authentication with 2FA apps like Google Authenticator, FIDO security keys like Yubikey and SMS messages.
You can also use more than one second factor authentication method with your accounts to ensure continued access.
2FA Enforcement
You can enforce 2FA support for all your team members, ensuring there are no weak links in the chain.
Personal Token Restrictions
While Personal API Tokens can be a conveniet way to test your API clients, they can also be a security weak point. These can be disabled across your account for all team members with access to your API endpoints.
Toolbelt Login Restrictions
You can use the Cloud 66 Toolbelt (CX) to sign into your account with ease (use cx login) While this feature makes logging in very quick and easy, it can be disabled across all of your accounts if you run the Toolbelt in an environment you don't fully trust.
Fine-Grained ACL
All team members in your team can have fine-grained Access Control Lists through Roles and Permissions. You can grant and deny each of them aribitrarily different levels of access to specific parts of your accounts and operations.
Service Accounts
To avoid password sharing and losing access when members leave your team, you can use a Service Account for your API and command line access. Running this kind of shared access through a headless, standalone account allows for better control and security.
sudo Mode
When performing potentially dangerous operations, the system will ask you for your second factor authentication to enter a "sudo mode".
Audit Records
All actions of all team members and Cloud 66 support staff are recorded in Audit Records and are accessible to view and search by the account owner.
Anomaly and Account Takeover Detection
All user activity is monitored for abnormal behaviour and signs of account takeover. Users are notified and might be presented with more login challenges in such cases.
More info:
- Link to blog: Cloud 66 Security Features
- Link to blog: Service Account
- Link to docs: Enabling two-factor authentication (2FA)
- Link to docs: Security Summary
- Link to docs: Audit log for account activities
- Link to docs: Toolbelt Easy Login + Access Control
