I'm really pleased to highlight one of our key security features: Cloud 66 Account Protection. In an era of phishing antics, rogue apps, malware and key logging attacks, we believed a revised approach was required to how we log, authenticate and provide access permissions to Cloud 66 users based on their device attributes, location and even the security of their network.
Cloud 66 has built-in added protection for all users in an effort to mitigate your account from being compromised. To achieve this, we capture every user action regarding how you and your team interact with us, to establish common usage behaviors.
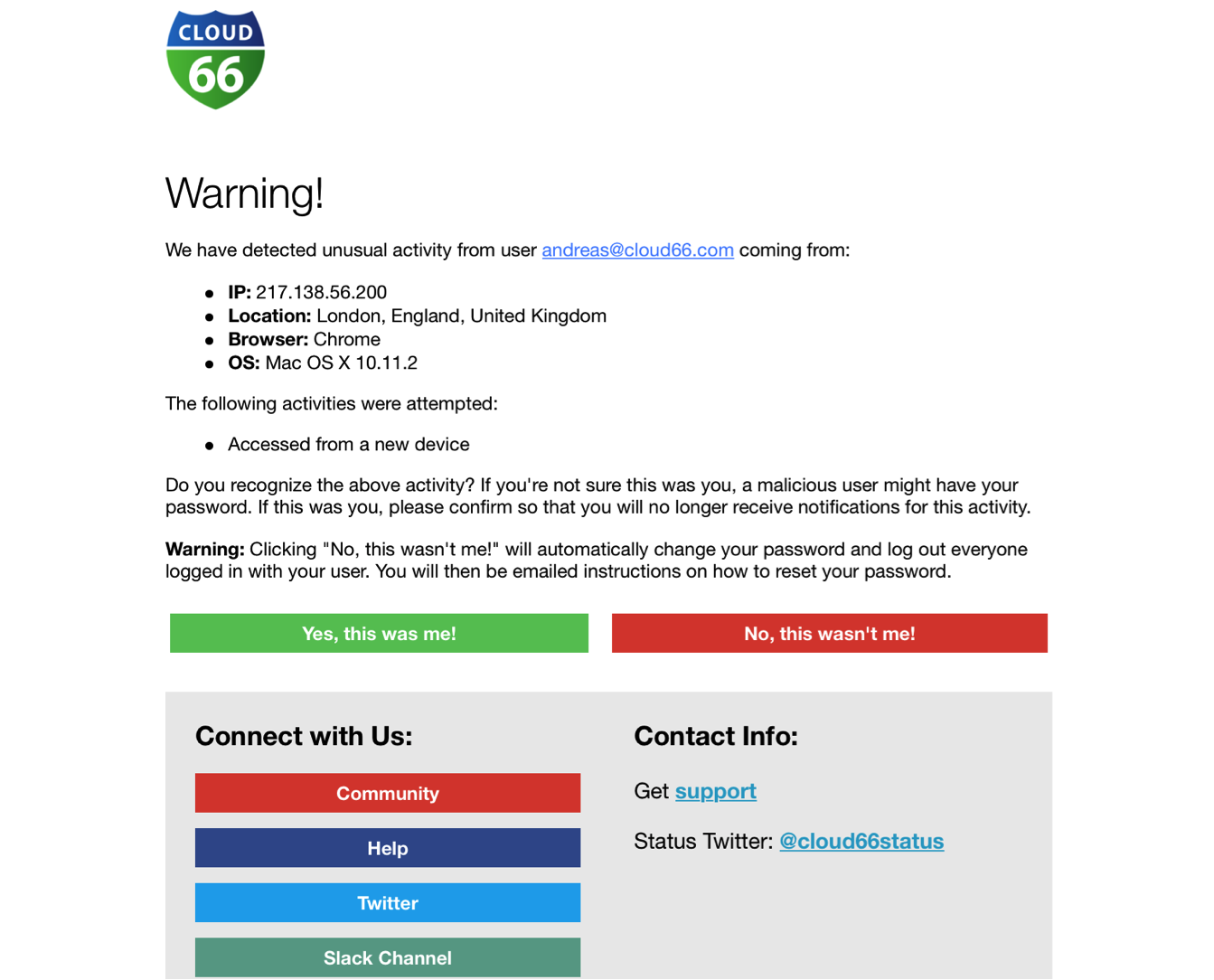
Analyzing the devices, locations and usage patterns typical to the way you use the Cloud 66 service allows us to detect when access attempts become inconsistent. When things look out of the ordinary (i.e. logging in from a foreign IP address, repeated failed attempts, etc… ), we’ll send the owner of the account an email with a brief explanation of what we’re seeing, allowing you to make a judgment call on actions needed.
While having the right access credentials i.e. username and password may seem like the obvious starting point to validate authenticity, it’s not always foolproof. Thanks to our ability to monitor and log user behaviours, we can mitigate the risk of security breaches by maintaining detailed user logs, applying multi-factor authentication, and screening IP credibility for suspect behavior to protect your account against rogue access attempts.
Happy Days.
